A Keystroke recorder or keyboard recorder captures and records what a user types on your computer. (typically without the user knowing)
With a computer keystroke recorder, a software can log emails sent, passwords entered, websites visited, private chat conversations, file inputs, and much more!
Every keystroke recorded is logged to a confidential file for later examination.
Keystroke logger/ recorder is used by employers, security professionals, parents, and network administrators to manage and track their computer usage behind their backs.
A keyboard recorder is also known as a keystroke recorder or keylogger and can be either software or hardware. While the programs are legal, the keylogger is used for stealing passwords and other confidential information.
How Keystroke Logger Works
Just like a disguised surveillance camera, a keylogger records keys as you hit them on your keyboard. Keystroke loggers reach as any other malware and are hard to uncover.
You can get contaminated by merely visiting a website.
Also, some keylogging software can seize screenshots of your movement and record your microphone.
When you establish and run the software in the system, it begins scanning each activity of your employees. You can install it in numerous ways by picking hardware or software loggers.
And the IT department holds the authority of this software and can access its records hassle-free.
Keystroke logging works by tracking & registering every keystroke entrance on a computer. It is often done without the permission or knowledge of the user.
A “keystroke” is an interaction with a button on your keyboard.
Keystrokes tell your programs what you want them to do; it is how you “talk” to your computers.
These commands include:
- Length of the keypress
- Time of keypress
- Velocity of keypress
- Name of the key used
Benefits of Keystroke Loggers
1. Insider Threats
The keystroke recorder secures confidential data from insider threats if any, along with tracking keyboard usage.
Since corporate data theft is rising, you cannot trust anyone in your firm regarding accessing crucial data. Hence, these recorders benefit by tracking insider threats and protecting your data and reports.
2. Recorded Reports
Keyloggers are terrific assistance in registering the reports of the completed projects in their cloud storage for project managers to access it anytime to inspect the employees’ productivity.
3. Productivity Tracker
One of the best advantages of keyloggers is tracking employee productivity(especially in the remote work structure). A keystroke recorder can support maintaining the work balance for the management teams by distinguishing between the productive and non-productive workforce.
4. Time Management
Another positive of keystroke recorders is tracking the time of their employees. These keyloggers are super-efficient applications tracking the log-in, log-out time details, and the total working hours of employees. Such specifications benefit the management a lot in holding the productivity graph of the entire organization simultaneously.
5. Employee Activity
Employers can monitor employee activities, total time taken to finish an assigned task, including the work approach they follow.
EmpMonitor is the best employee monitoring software for monitoring employee activities in remote work.
EmpMonitor is impressive with complete 360 degrees monitoring of all the workflows across all the departments
Additionally, it has remarkable features for promptly checking on the project progress status.
Some Key Features-
- Time Management– This feature tracks the employee’s presence and their activities, spot and eliminate wasted time.
- User Management– Effectively manage multiple systems and users through centralized network monitoring.
- Get real-time insights- You can easily check what your employees are doing in real-time, live refresh mode, and provide department-level management.
- Manage Attendance– EmpMonitor provides a flexible user-based setting(log hours from anywhere) that gives accurate work hours and department-wise attendances. In addition, you can extract ready-made reports for up to 30 days with an auto screenshots facility as well.
Project Management Functionality of EmpMonitor
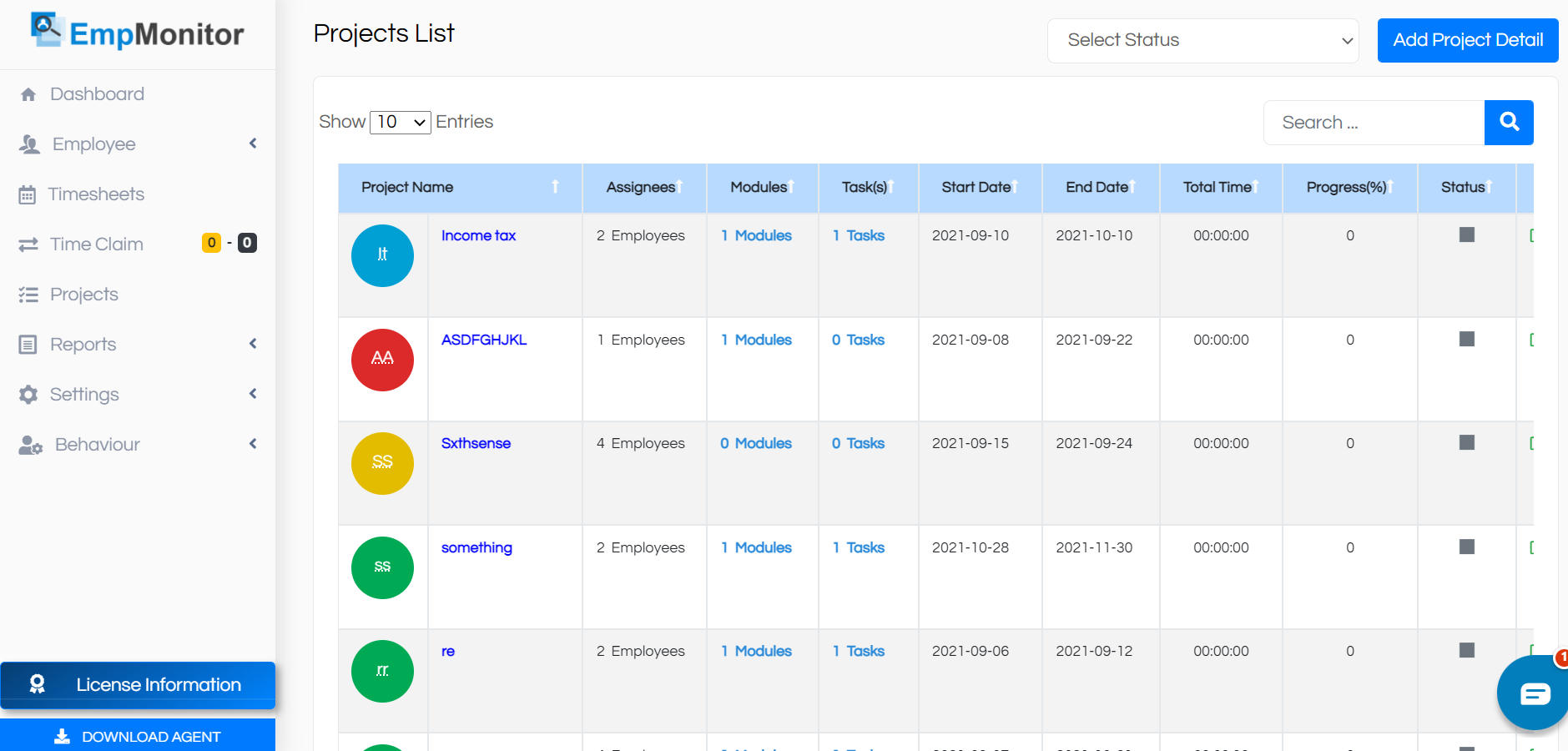
EmpMonitor provides project lists with project names, modules, tasks, start and end date of the project along with total time taken to complete a project. Also it gives updates on the progress of a project with current status.(See the image below)
Furthermore, it provides regular productivity hours with graphs to better understand the working patterns of your employees.(See image for productivity graphs)
Also, web app usage reporting
6. Transparency
After installing the keyboard recorder, the employers can scrutinize all the employees with complete transparency, enabling them to build a bridge of honesty in the establishment.
Uses for Keyloggers/ Keyboard Recorder(Keystroke Recorder)
4 main factors determine whether the keylogger/ keyboard recorder use is legally permitted, unlawful, or morally debatable. Let’s find out what they are-
- Degree of consent — This means the exact conditions under which the keylogger is used. Some of these are- 1) Clear-and-direct consent, 2) Hidden permission in the discrete language in terms of service agreement, or 3) no permission at all?
- Goals of the keystroke recorder — It determines the objectives of the keylogger. Whether it is to rob a user’s data for illegal uses ( such as identity theft or stalking) or what?
- Ownership of the product being monitored — Is the keylogger used by the device owner or product manufacturer to monitor its use?
- Location-based laws on keylogger use — Is the keylogger used with intent and consent in accordance with the law of the land?
Legal Consensual Keylogger Uses
Legal uses need the person/ organization to:
- Apply no criminal use.
- Be the product proprietor or legal guardian of a child maintaining the product.
- Operate it under the area’s governing laws.
Consent is absent here unless rules need them. (This encloses clicking “accept” to use public Wi-Fi or sign an employer’s agreement.)
For consensual matters, keystroke logging is allowed underneath exact wording within the duration of service or an agreement.
Here are some common legitimate uses for keyloggers(keystroke recorder):
- IT Troubleshooting– Details are collected on user problems to fix them.
- Computer Product Development — To gather user feedback and improve products.
- Business Server Monitoring — To watch for unauthorized user activity on servers.
- Employee Surveillance — To supervise safe use of company property.
Legal keyloggers are in our daily lives more than we realized. Fortunately, the power to control is in your hands if we are aware and the monitoring party has requested access.
Legal Ethically Ambiguous Keylogger Uses
Non-consensual legal keylogger usefulness is dubious for breaking the trust and privacy of those watched. (this type works in the bounds of the laws of the area)
In other words, a keylogger user can scan computer products they own and monitor their children’s gadgets lawfully.
But they cannot surveil instruments outside their ownership. (This leaves a bit of a grey area for all others engaged).
Without consent, people and organizations can use keyloggers for:
- Parental supervision of kids — to protect their child in their online and social activities.
- Employee productivity monitoring — to watchdog employees use of company time.
- Security –Even consent planted under legal nomenclature within a contract or terms of service can be debatable. However, this does not explicitly cross the line of legality.
Criminal Keylogger Uses
Illegal keyloggers use shuns consent, laws, and product ownership for shady purposes.
When utilized for criminal purposes, keyloggers serve as malicious spyware to catch sensitive details. Keyloggers record data like passwords or financial data for unlawful exploitation.
Criminal intent can apply in cases to:
- Stalk a Non-Consenting Person.
- Intercept and Steal Personal Info — such as credit card numbers etc..
Once the keylogger is used for criminal intent, they are malware. Security products may not label uncovered keyloggers as immediate threats as they account for the entire user case spectrum.
Why Keystroke Logging Is a Threat
Keyloggers can be a threat if collected sensitive data is not managed carefully and when you are clueless that what you type into your keyboard is being recorded.
This may inadvertently reveal:
- Passwords.
- Credit card numbers.
- Communications
Sensitive information like this can easily become an easy target for data theft and can expose saved keystroke logs, even in legitimate use cases.
This data can easily be leaked via an unsecured device or through a phishing attack.
Other cases of threat are common leaks by a direct criminal attack with malware.
Organizations containing abundance keylogging data are prime targets for a breach.
The criminal use of keyloggers can exploit your information by infecting it via download or other means.
How to Save Your Enterprise From Keyloggers(Keystroke Recorder)
Minimize the probabilities of keylogger injection by following these best cybersecurity rules.
1. Use a Virtual Keyboard
Virtual keyboards are onscreen keyboards that accept user commands instead of a physical keyboard.
A virtual keyboard is recommended for improving login security for financial services because their commands are much more difficult to intercept with keyloggers(keystroke recorder).
2. Use Multi-Factor Authentication
A strong password with multi-factor authentication can prevent cybercriminals from accessing sensitive data even if they have the keylogger records for passwords.
With multi-factor authentication, a user’s password is only a single component of an access chain.
Without the supporting authentication codes, login credentials alone are almost useless.
Furthermore, a password manager can strengthen a password policy by generating complex passwords and preventing password recycling.
3. Always Keep Anti-Spyware Updated
Up-to-date anti-spyware & antivirus software is competent in catching the latest keystroke logging menaces across most operating systems.
4. Ensure Encryption for Wireless Keyboard Signals
Wireless keyboards (operating unencrypted radio communication protocols) are efficiently intercepted by remote keyloggers. Ensure wireless keyboards utilize encrypted Bluetooth technology.
5. Use a VPN and a Firewall
Like antivirus software, VPNs must be maintained and revised so that they can catch the latest keylogger hazards as VPNs and firewalls can detect and block endeavors to install malware into your ecosystem.
6. Monitor Entire Attack Surface for Vulnerabilities
Keylogger attackers depend on digital vulnerabilities to infiltrate their malware.
Attack surface monitoring software is competent in scanning susceptibilities across both internal and entire third-party vendor attack surfaces that could loosen keylogger injections.
7. Be Skeptical of All Messages
Be skeptical of all messages including, emails, text messages to mobile devices, and even social media inquiries.
8. Prevent Files & Applications from Self-Running
Disable self-running files to contain hardware keylogger(keystroke recorder) attacks.
USBs packed with keyloggers lean upon this automatic initiation feature to immediately deliver their keystroke logger malware once connected.
If anything seems too cynical, always confirm its legitimacy by reaching the sender directly.
9. Educate Employees
Employees are the most common attack vectors in every cybersecurity program, so you must train them about possible threats.
Train them about the use of keyloggers(keystroke recorder) and how to determine cyber threats.
Is It Legal
Yes, monitoring the employees’ keyboard and internet usage is legal, but it should be apparent when an employee joins the company.
All surveillance conditions and terms are mutually discussed transparently before joining.
Furthermore, employees need to understand that it’s strictly professional not personal surveillance and the aim of the firm is not to circumvent privacy but to uphold the establishment’s productivity.
How to Check for a Keylogger on Your PC
A keyboard recorder can be tough to uncover. Regardless, the first symptoms of an infection could be:
- Web page performance slowing down.
- Your mouse or keystrokes pausing or not showing up onscreen what you’re actually typing.
- Getting error screens when loading web pages or graphics.
Here are the steps you need to take:
- Run an antivirus scan to detect malware and keyloggers/ keystroke recorder.
- Open Task Manager and check for any suspicious applications.
- Check your list of installed programs – run a google search if you have doubts.
Also Read-
Working Overtime: How to Know it is Working for You? (2022 Update)
Key Takeaways
- With the digital products handling dominance of our lives, we are leaking out a lot of highly-sensitive information on our devices.
- If you are an entrepreneur struggling with employee monitoring and low productivity issues, a keystroke recorder is a perfect resolution for your business requirements.
- A comprehensive internet security solution is a reliable route to safeguard your business and personal interests to defeat keylogging.
- The management ought to investigate the productivity and safety of the organization by seating keystroke loggers in the user’s systems to maintain a check on the keyboard usage of the employees.