The modern business conditions are entirely distinct from what was usual just 20 years ago. The world we live in is an information age. When you look around, you will find that even the basic activities are deeply integrated with technology.
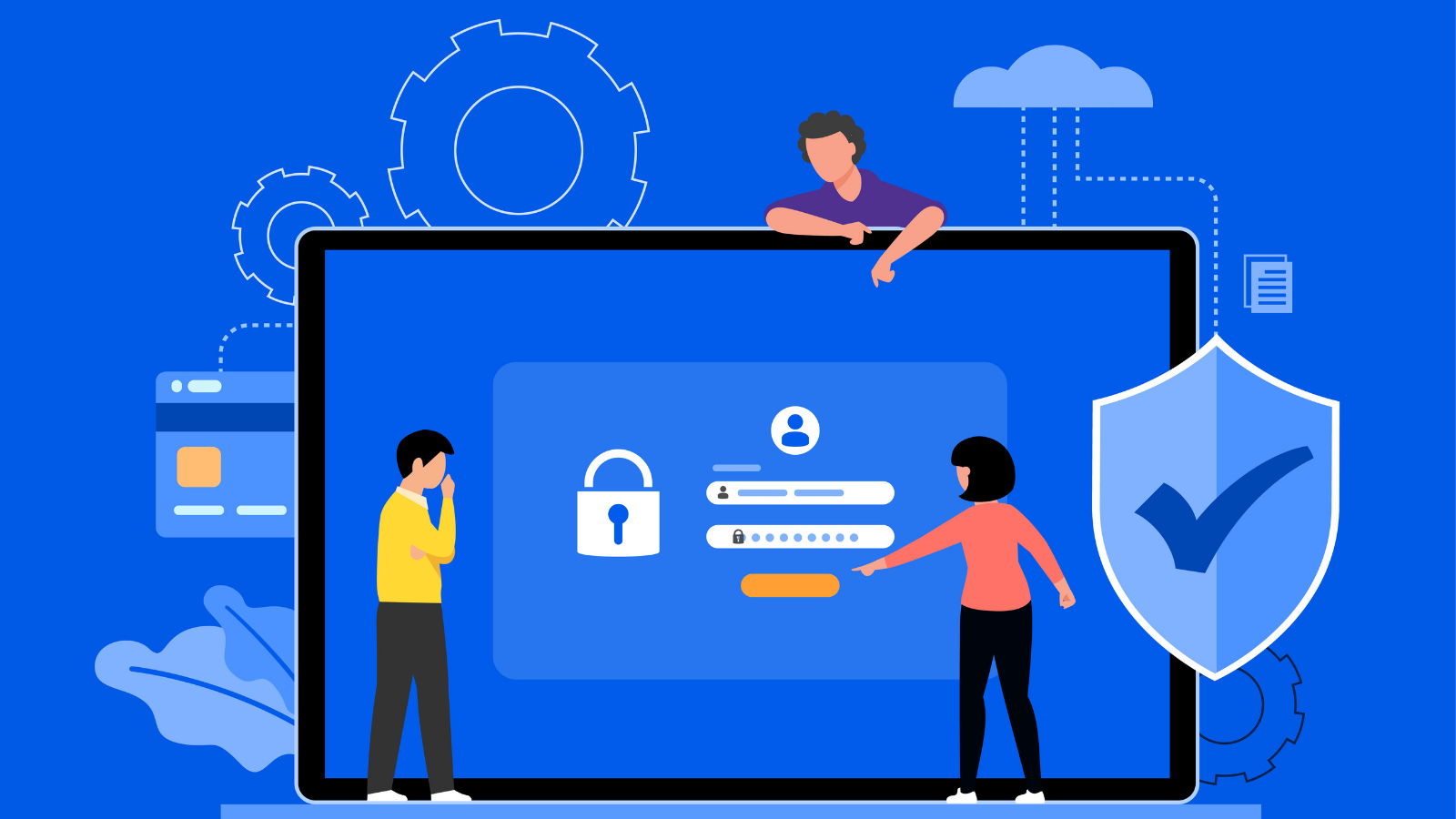
Running a business is no longer about delivering quality services or products, it is also about protecting your data and implementing confidentiality. Identity and Access Management refers to the IT security discipline, framework, and solutions for handling digital individualities.
Access management systems provide an extra layer of security over your business’s network. It gives control over which groups of employees have access to which applications. IAM systems are as easy or intricate as you required them to be with customization possibilities for revealing certain files, documents, records, and more.
Hit The Play Button To Listen Podcast:
If your company has numerous departments with unique roles, implementing IAM services is proactive. Only employees you require can progress forward through a company portal, and they’ll be able to see only the appropriate information. In this article, we will discuss everything you need to know about identity and access management. Let’s dive in!
What Is Identity And Access Management?
In simple words, identity and access management is a structure of business processes, policies, and technologies that aids the management of electronic or digital identities. It helps administrators to control user access to critical information within their organizations.
IAM systems include single sign-on systems, two-factor authentication, multi-factor authentication, and privileged access management. It also provides the ability to store and share appropriate data.
You can deploy IAM systems on-premises by a third-party vendor through a cloud-based subscription model or a hybrid model.
On a fundamental level, IAM includes the following components:
- Employee identification in a system.
- Task identification in a system and assigning tasks to employees.
- Adding, removing, and updating individuals and their roles in a system.
- To assign levels of access to individuals or groups of individuals.
- Protecting the sensitive data within the system and securing the system itself.
The implementation of identity and access management technology
ensures the safety of your sensitive data, and it protects it from an outside party who can potentially view, steal, or manipulate sensitive business data.
How Do Identity And Access Management Work?
Identity and access management (IAM) ensures that the relevant people and job roles in your organization (identities) can access the tools they require to do their jobs. Identity management and access systems empower your organization to maintain employee apps without logging into each app as an administrator.
Identity management solutions generally perform two tasks:
- IAM verifies that the user, software, or hardware is the same as they say they are by authenticating their credentials against a database. IAM cloud identity tools are more secure and flexible than traditional username and password solutions.
- Identity access management systems grant only the appropriate level of access. Instead of a username and password allowing access to an entire software suite, IAM allows for narrow slices of access to be portioned out, i.e. editor, viewer, and commenter in a content management system.
What Is The Difference Between Identity Management And Access Management?
Identity management verifies your identity and stores information about you. An identity management database stores your information such as your job title and your direct reports – and authenticates that you are, indeed, the person described in the database.
Access management utilizes the stored identity to determine which software sets you’re allowed access to and what actions you can perform when you access them. For example, access management will ensure that every manager with direct reports has access to an app for timesheet approval, but not so much access that they can approve their timesheets.
Benefits Of Identity And Access Management:
Identity and access management is the information security practice that allows users access to relevant technology resources as required. It includes three major concepts: identification, authentication, and authorization. Together, these three processes combine to ensure that specified users have the access they need to do their jobs while securing sensitive resources and information from unauthorized users.
-
Secured Multi-factor Authentication:
These include technologies like Iris Scanning, Fingerprint Sensors, Face Recognition, and much more. Multi-factor Authentication (MFA) ensures that the user provides at least two sources of evidence to confirm their identity. This leads to a reduction in the risk of identity theft.
-
Eradication Of Weak Passwords:
Numerous data breaches result due to passwords that are either stolen, default, or weak. By implementing best practices in credential management, Identity and Access Management systems can effectively eradicate the possibility of a weak password being set by a user.
-
Advanced Tracking Of Malicious Activity:
State-of-the-art IAM systems offer advanced tracking of malicious behavior using Artificial Intelligence, Machine Learning, and risk-based authentication. This enables organizations to prevent online attacks and avoid financial loss.
-
Affordable Security Expenses:
IAM assists in reducing the amount needed to invest in security. For example, a Cloud-based Identity and Access Management solution diminishes the requirement of an on-premise foundation.
-
Increased Security Measures:
With the help of IAM technologies, organizations can efficiently distinguish and alleviate the risks associated with security. Such technologies allow instant access revocation to all business-critical systems for those who are in charge.
-
Easy Distribution Of Security Policies:
This particular feature of the IAM model provides a common platform to apply security policies to all organizational systems with ease.
-
Profitable Collaboration With The Government Norms:
IAM solutions let firms display that their information is not being ill-treated. The data required for auditing gets provided by these organizations. Thus IAM solutions ensure adequate compliance of firms with government regulations. The company and the government mutually benefit due to these solutions.
-
Improved Data Security:
Consolidating authentication and authorization functionality on a single platform provides IT professionals with a consistent method for managing user access. When a user leaves an organization, IT administrators may revoke their access to the centralized IAM solution with the confidence that this revocation will immediately take effect across all of the technology platforms integrated with that IAM platform.
-
Access Management Reduced Security Costs:
Using a single IAM platform to manage all user access allows administrators to perform their work more efficiently. A security team may have some additional upfront work integrating new systems into an IAM platform but may then dedicate time to the management of that platform, saving time and money.
-
More Effective Access To Resources:
When users receive access through a centralized platform, they benefit from the use of single sign-on (SSO) technology that limits the number of interactions they have with security systems and increases the likelihood that their legitimate attempts to access resources will succeed.
With the help of the EmpMonitor, you can monitor every activity of your employees during office hours. It will help you to measure and ensure that they meet the productivity benchmarks.
Enforce Security And Improve Productivity With EmpMonitor:
EmpMonitor is a cloud-based automatic work time tracker app and employee monitoring system that calculates the productive and idle hours helps for measuring the productivity of your organization and employees.
EmpMonitor monitors every activity such as logging in, break time, idle time, web pages accessed, etc. All this information helps you to measure the productivity and efficiency of employees.
It provides accurate details of productive hours with just one click. It also offers an option to export the data in timesheets in the required format, which helps to minimize human error, and you can monitor every activity of your employees from a single dashboard.
EmpMonitor offers many useful tools to ensure the productivity and efficiency of your employees:
- Time Tracking:
With the Help of EmpMonitor, you can track every minute of your employee’s working hours. It gives you a detailed report on how much time they have been active, idle, neutral, or offline from a single dashboard.
- Productivity Tracking:
Empmonitor allows you to identify the productivity killers and provide a clear understanding of every process from end to end. You can track and measure the productivity of your employees.
- Regular Screenshots:
EmpMonitor captures screenshots of your employee’s system. It keeps them in check that they are working on assigned tasks and not scrolling through cat videos.
- Keystroke Logging:
Keystroke logging is one of the best ways to ensure data security. It lets you know about the words that employees type
Check Our Latest Blogs:
How To Monitor Employee Internet Usage?
Is managing remote employees more difficult than ever in this WFH culture?
Why Do Corporations Need Any Kind of Tracking on Employees?
Wrapping Words:
Identity and access management systems are an integral aspect of the industrial world as they contribute to efficient and secure data and resource management. They have multifarious tools and technologies that aid in the safe and controlled distribution of resources across a company network. Numerous benefits of Identity and Access Management make it a one-stop organizational solution.
With the upsurge in diverse cybercrimes, organizational security becomes exigent. Identity Access Management solves the problem at hand and also reduces the costs involved in building secured systems. It enhances productivity, making it the best option when it comes down to organizational security and management.